Portfolio
With 12 years of experience, I’ve navigated diverse challenges — applying best practices that place people at the center.
Maintaining Public Safety with Facial Recognition
The race to redefine the future of security software was on, and the shift away from on-premise to SaaS solutions was transforming industries across the board. For NEC, the goal was to take their #1 NIST-ranked Facial Recognition engine, build it as a state-of-the-art SaaS product.
My Responsibilities
> Research
> Sketching
> Object Mapping
> Wireframing
> Design System
> UI Design
> Testing
Agile Scrum Team
> Lead UX Designer
> Product Owner
> 2 Software Engineers
> Platform Architect
> 2 UI Designers
Type:
> B2B Product Design
Timeline:
> 12 Months
Design an advanced facial recognition solution, enabling security personnel to proactively monitor and respond to public safety threats.
My Role
As the lead UX Designer, in the Business Incubation team at NEC, I spearheaded the end-to-end design product design initiative.
Results
✓ Pilot launched and released.
✓ Usability tested with industry experts.
✓ Team effort recognized.
Research
To get started, I lead interviews with product leaders to produce an understanding of what the product vision is, who are the users, and the use cases we needed to cover.
Product Vision
For Security Personnel, at commercial business, who need to maintain a safe and secure business environment, our solution is an AI-driven video analyzing solution that identifies people, recognizes patterns and makes predictions. Unlike others in the market our Facial Recognition engine is ranked the highest performing by National Institute of Standards and Technology (NIST).
Use Cases
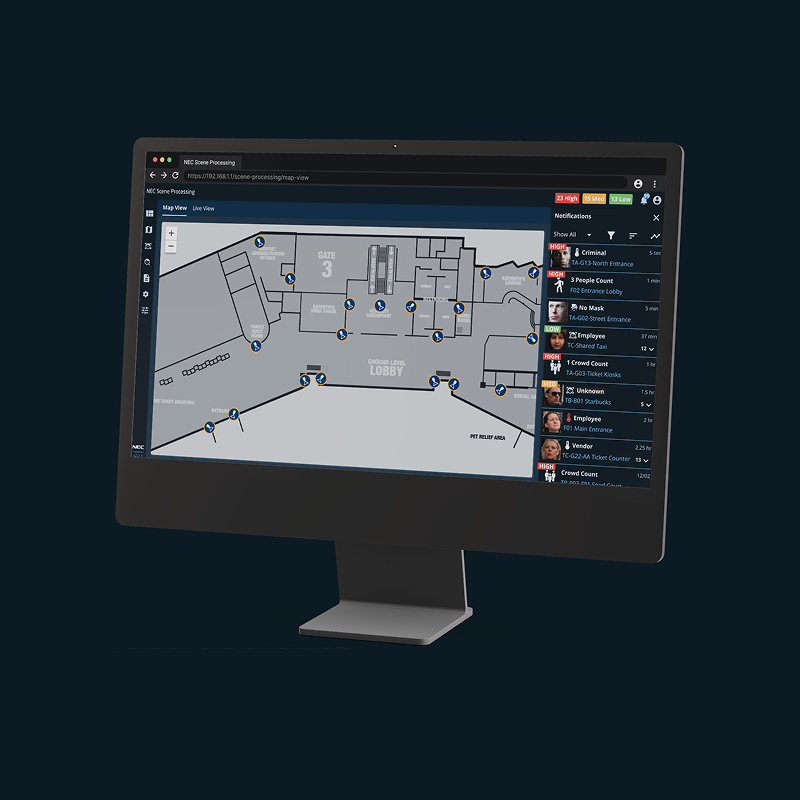
Face Detections
Recognizes people’s faces and estimates age & gender.
Counting the # of people that pass by a defined region.
Crowd Detection
Detect when people are in close proximity within a set time.
Counts the number of people with no mask passing a defined region.
Actors and Users
The interviews uncovered various user actors to consider, however not all actors are users, here is how I differentiated them.
Security Personnel
Job Executor
Responsible for assessing and eliminating public threats. May coordinate with security personnel in the building or security room. Titles include security guard, loss prevention officer, patrol officer, etc.
Needs
- Monitor people and situations.
- Control traffic at entry points.
- Coordinates with other security personnel.
IT Leadership
Purchase Influencer
Responsible for individual or combined activities related to the job such as; integrating and maintaining the solution. May also oversee operations and security. Titles include CTO, Director of IT, IT Manager.
Needs
- Integrate solution within secure network.
- Connect solution to building security cameras.
- Estimate costs such as hardware, networking. processes, and training.
Head of Security
Job Overseer
Monitors the job to ensure the solution results meet the business objectives by tracking metrics and viewing reports. Titles include COO, Head of Security, Operations Manager.
Needs
- Understanding solution ROI.
- Managing security costs.
- Reducing public safety risks.
The Job Executor
Our target users would be Security Personnel, who execute the Job-to-be-Done of:
Maintaining a safe and secure business environment for customers in the building.
Design a unified but flexible application interface that helps Security Personnel to identify people, recognize patterns, and make predictions in order to increase public safety and security?
Comparative Analysis
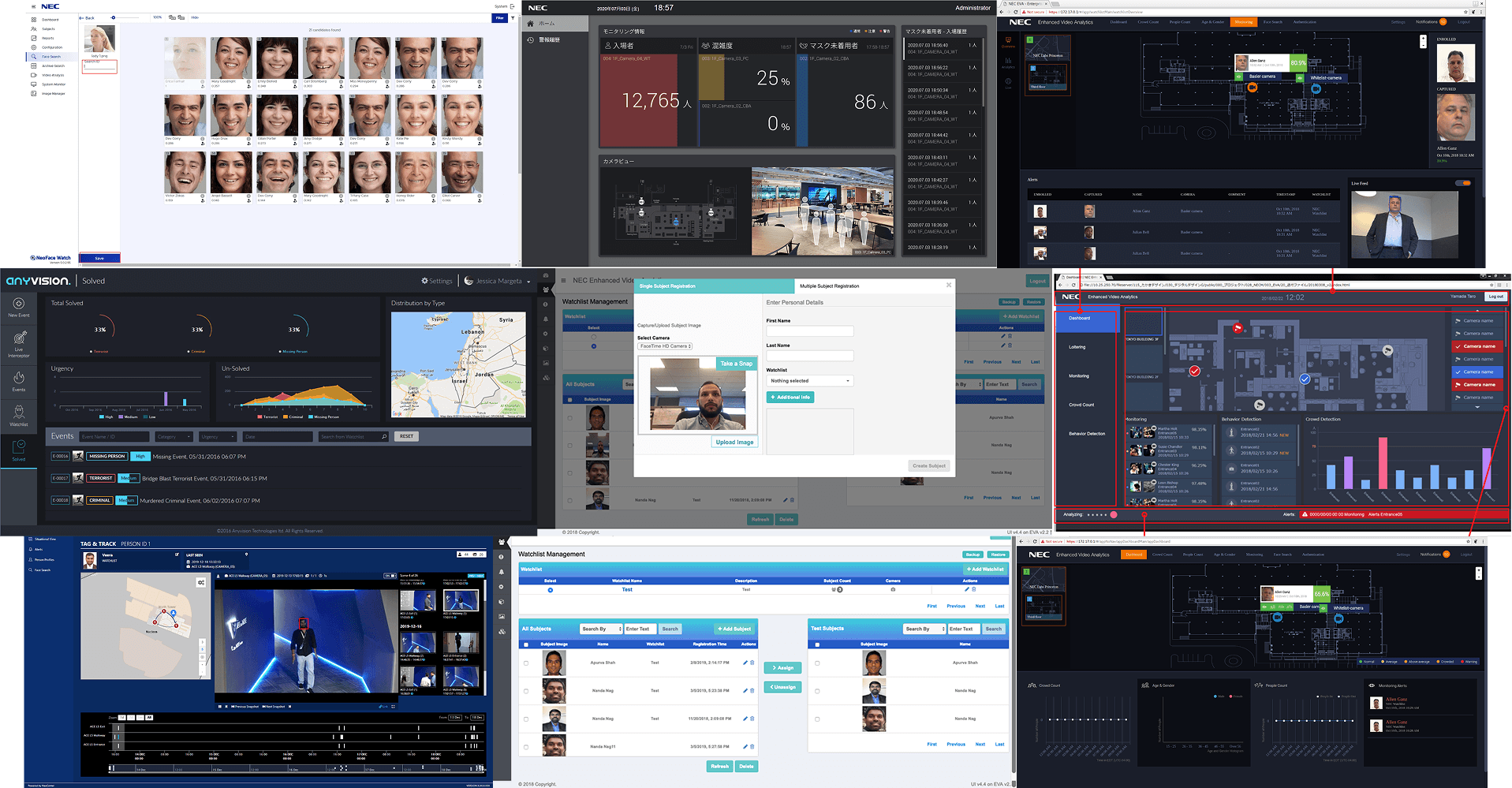
The design phase started with a review of existing NEC applications that performed similar use cases. This instrumental to attain an idea for the user flows expected and layout of the interface.
Sketching
I sketched wireframe flows when planning depicting the action elements that moved user through application accomplishing tasks.
Sketching played a key role when quickly iterating user flows via wireframe flows and screen layouts. I moved back-and-forth between sketching screens and sketching the user flow, each one informing the other.
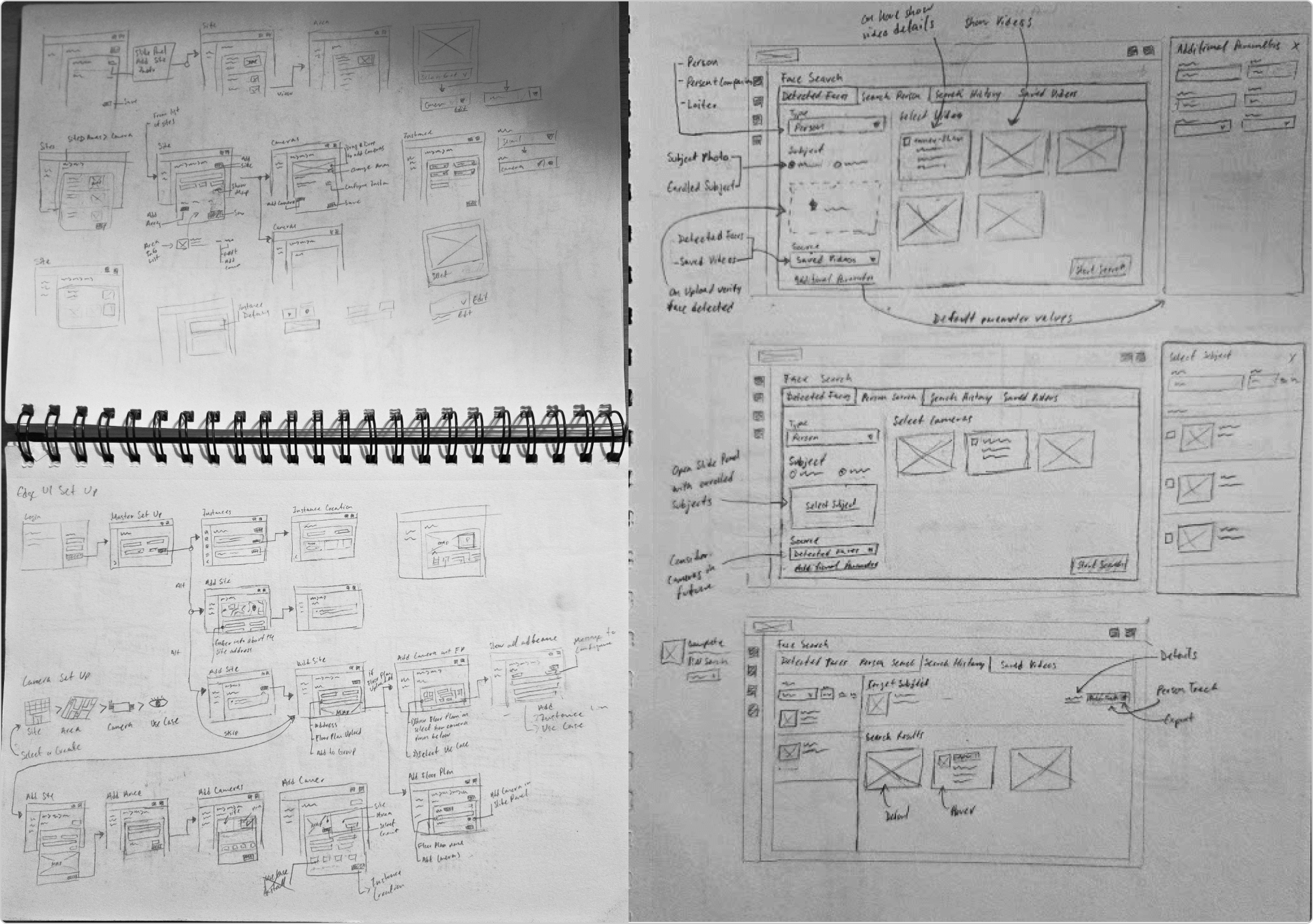
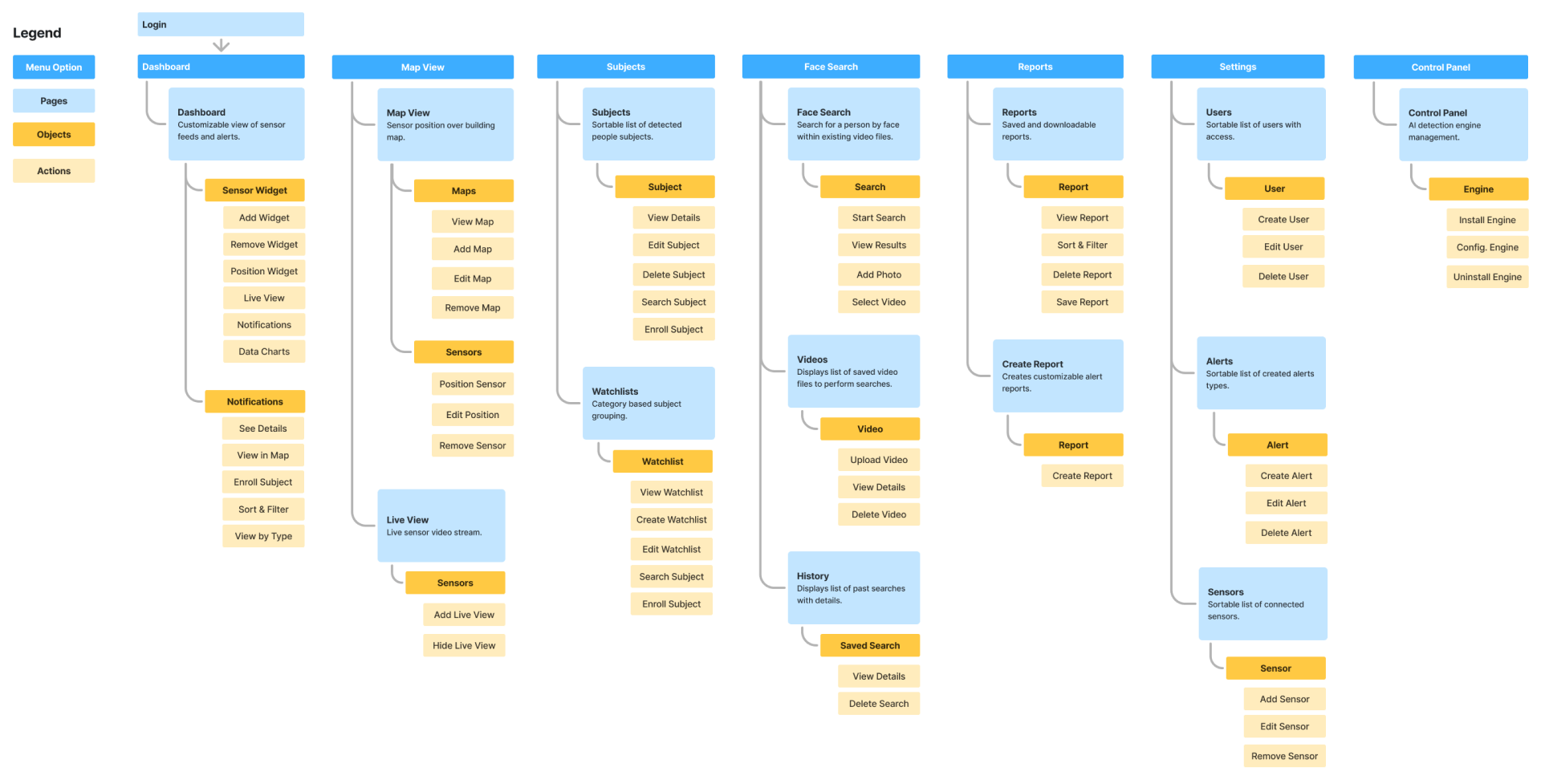
UI Object Mapping
I worked with the product owner and engineering manager to ensure we took account of every part of the application that needed to be designed. This Object Mapping exercise laid out key aspects of the product .
Wireframing
At this point, we had a good idea of how the application would function and what it could look like. It was time to start formalizing the wireframes. I collaborated with the two UX designers on the team, responsible for designing different parts of the application, to create flexible layouts that would accommodate the most screens.
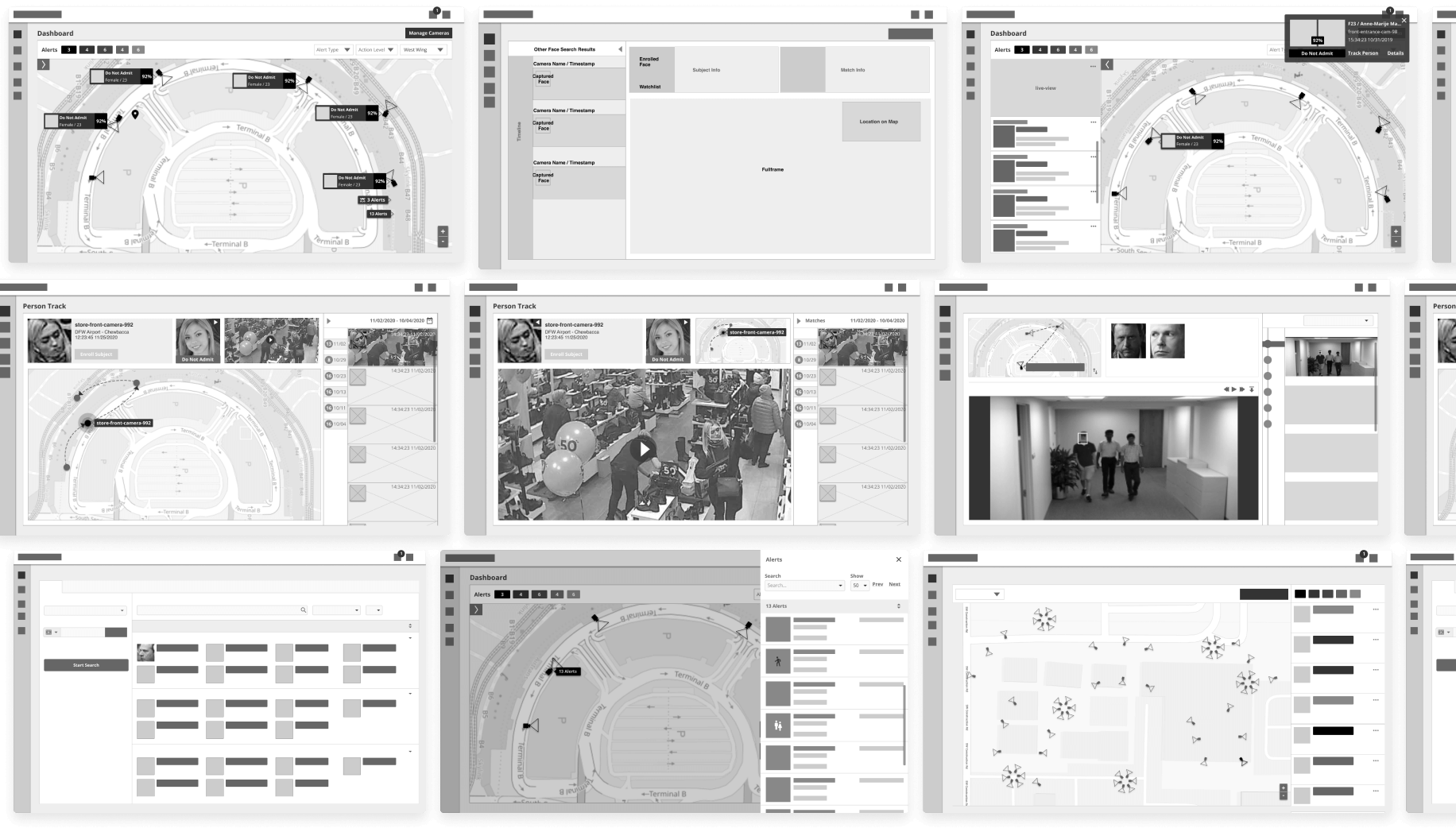
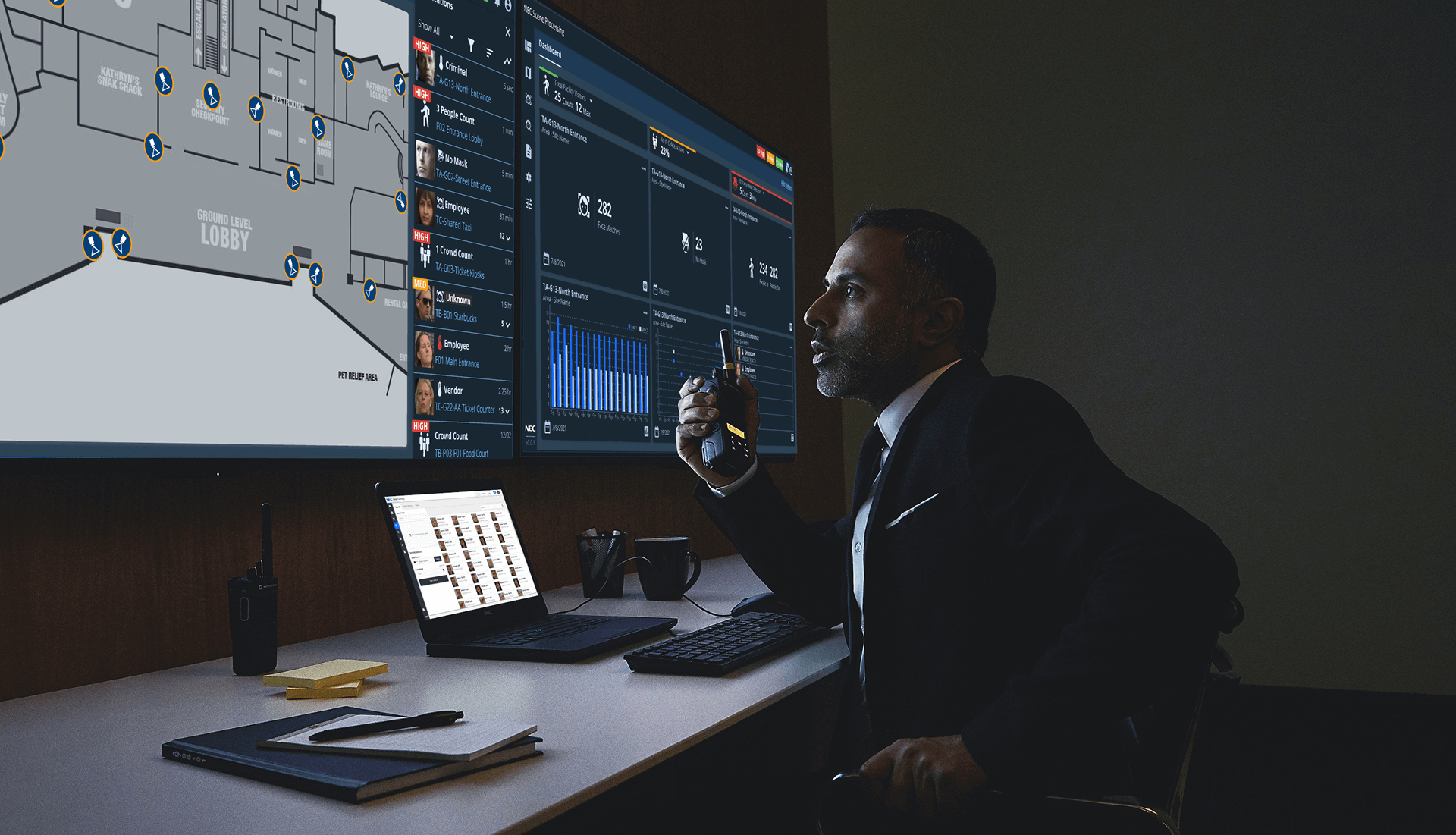
Prototyping Interactions
Some screens required several steps for users and needed a prototype to demo with engineering. This particular screen shows three flows.
1
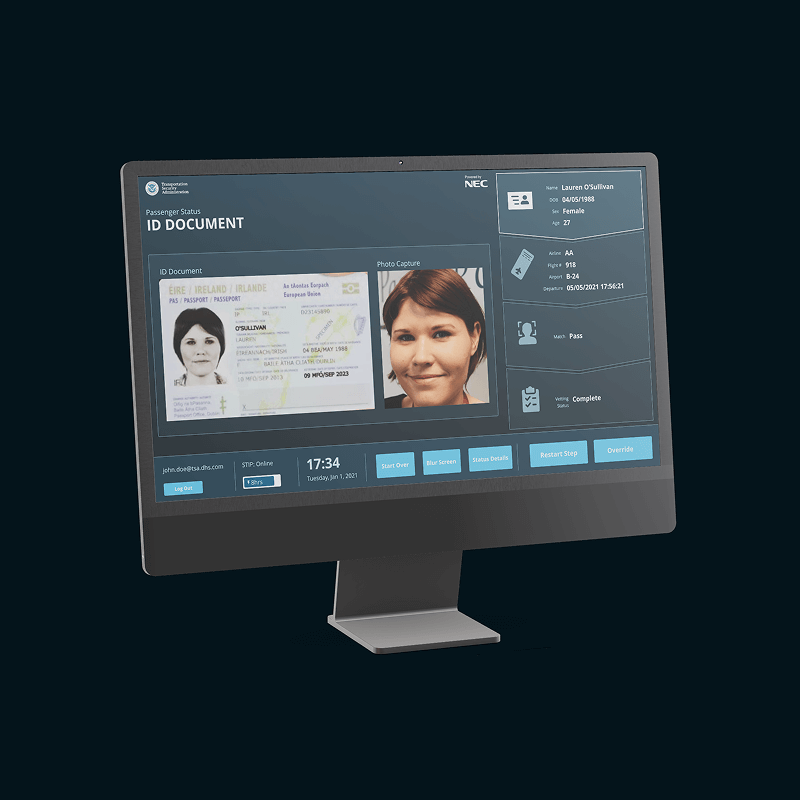
Cameras can be placed on a map of the building, enabling security personnel to view the live stream and list of faces detected.
2
Face detection alerts can be viewed with the subject’s information and history of detections, enabling security personnel to quickly assess the threat.
3
Switching to a map where an alert has occurred, enabling security personnel to know where the subject is located.
Testing with Users
I recruited users that fit the security personnel persona for usability testing. Each participant was given a scenario to perform while being recorded. The test was conducted using a work-in-progress version of the application as well as click-through prototypes.
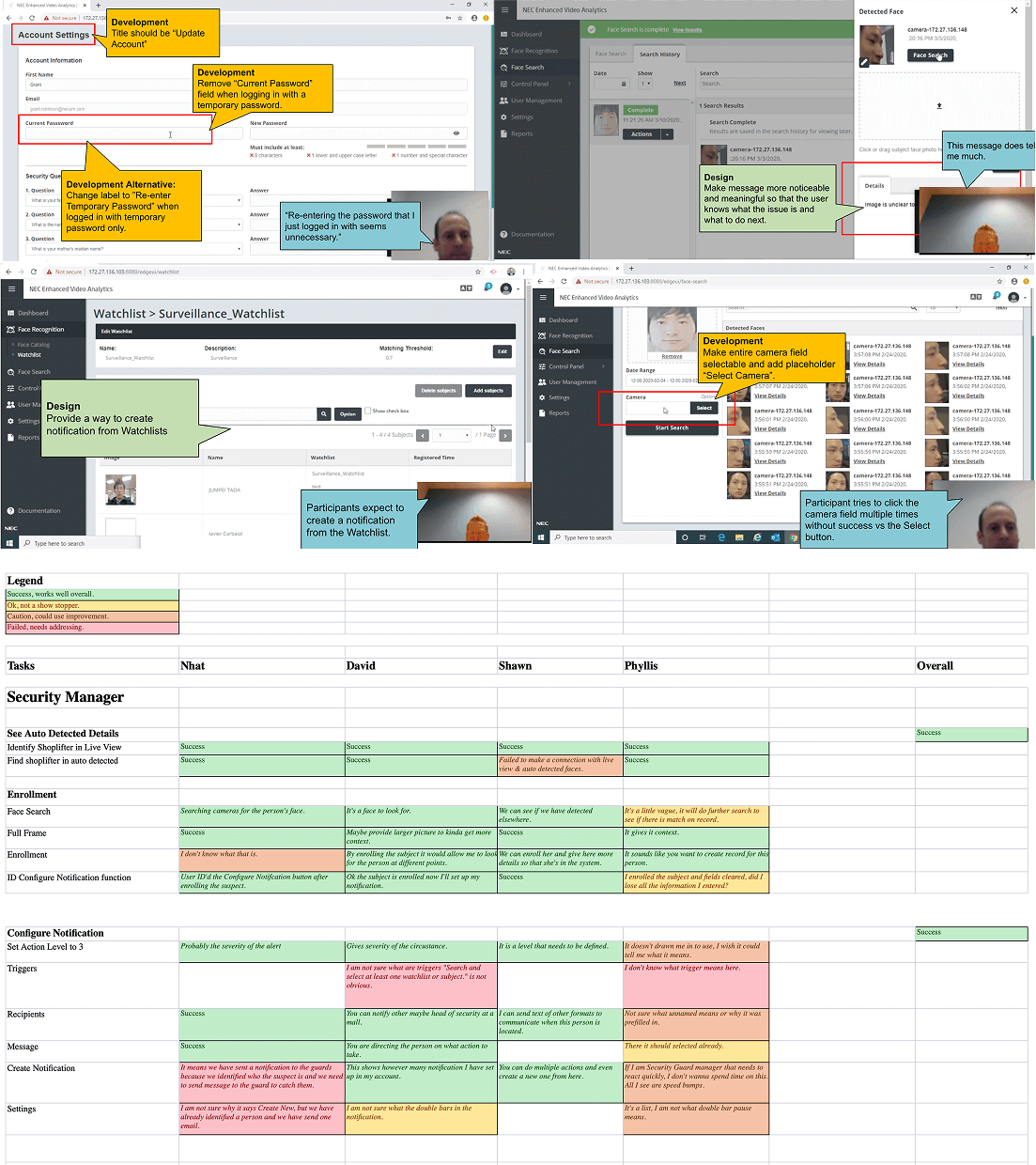
Scenario
A an unknown suspect entered the building. As a Security Officer, create notification to track the person’s movement through the building.
Results
4 out of 5
Participants successfully completed the scenario. Additionally the notification creation flow need work.
User Quote:
I am impressed with how fast the face detections appear and ability to view details.
– David H., Director of Asset Protection (Retail)
Design System
Improvements from the usability study were bundled up with design consistency updates. In collaboration with the two UX Designers, we formalized a design system to be applied as we prepared for a major release.
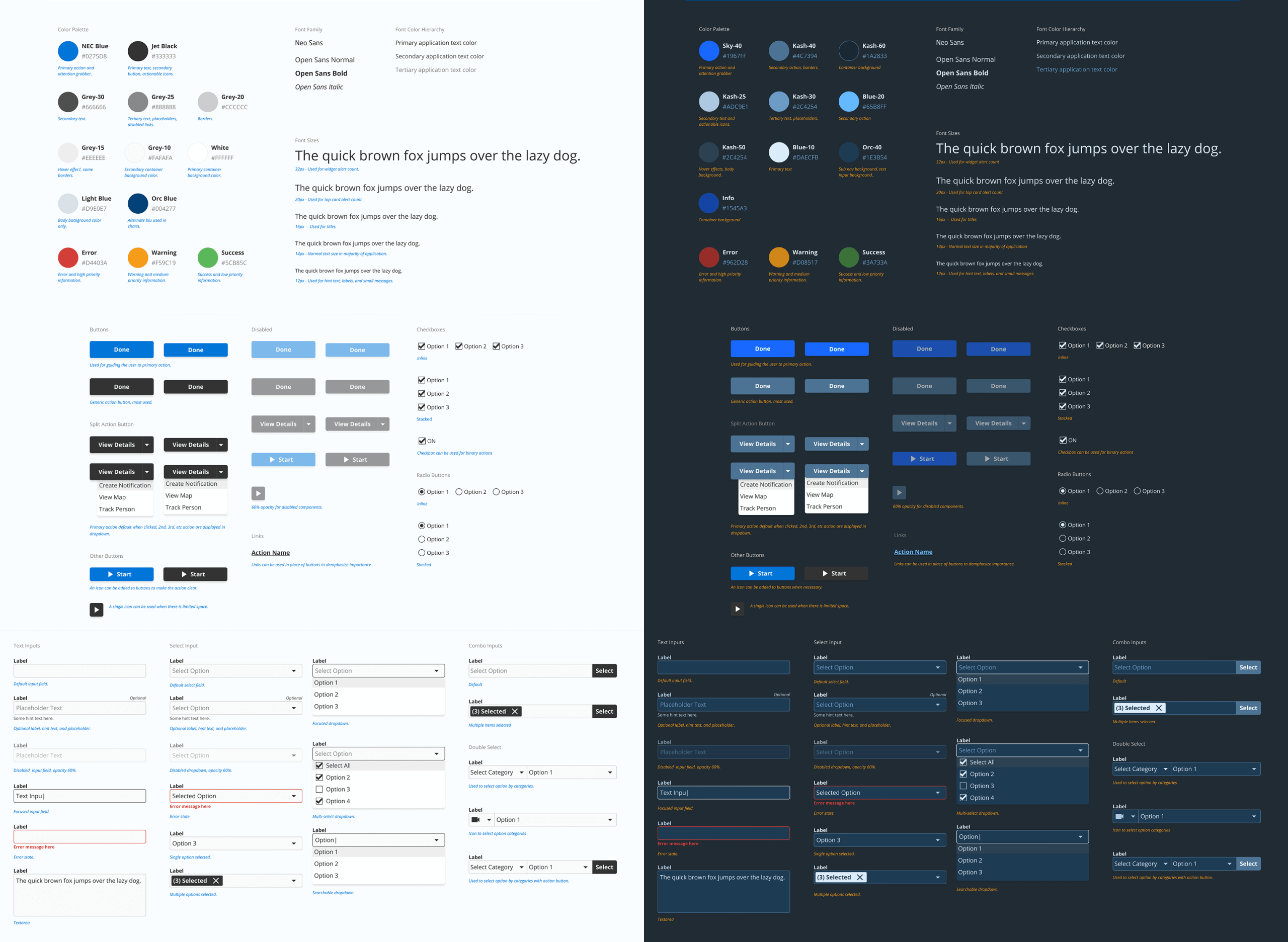
Conclusion
The product beta version was released and made available for piloting with exclusive partners. Our team received a token of appreciation for the work.